Stop Hoarding: Data Retention & Deletion Imperatives for Risk Mitigation

Written by Gimmal Product Marketing
At Gimmal, our mission is to help organizations effectively manage information, reduce risk, and ensure compliance in an ever-evolving regulatory landscape. In a recent webinar, our panel of industry experts dove deep into the critical topic of risk mitigation in information governance, especially amid the surge in data privacy laws and the persistent problem of ROT (Redundant, Obsolete, and Trivial data).
The Growing Challenge: ROT Isn’t Going Away
ROT—Redundant, Obsolete, and Trivial information—remains a pervasive challenge. With data volumes exploding, organizations often let ROT pile up due to a lack of ownership and fear of deleting something “just in case.” While storage costs may seem low, the total cost of ownership—including legal and compliance risks—can be significant.
Takeaway: ROT increases exposure to litigation, data breaches, and regulatory penalties. It’s not just a storage issue; it’s a business risk.
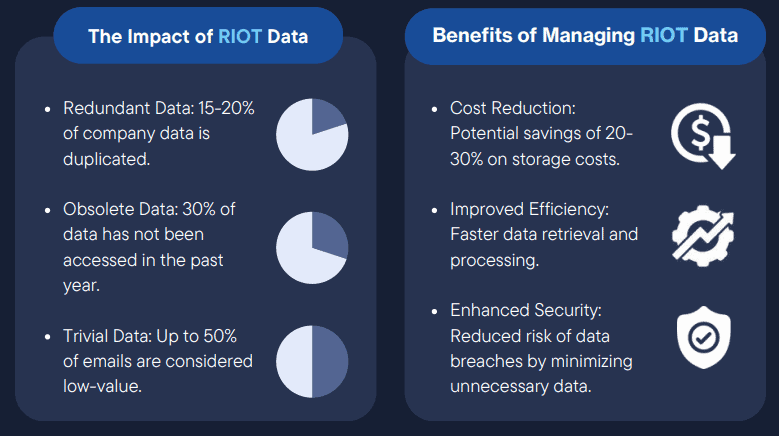
Sensitive Data: It’s More Than the “Usual Suspects”
The definition of sensitive data continues to expand. While most organizations protect classic identifiers (SSN, driver’s license, etc.), new regulations (GDPR, CCPA, and more) include broader categories:
- Biometric data
- Geolocation
- Inferred data from AI/ML models
- Corporate-sensitive information not explicitly covered by statute
Convenience copies of sensitive data—exports or downloads left on file shares—are frequent sources of breaches. Official systems of record might be secure, but scattered copies are a major vulnerability.
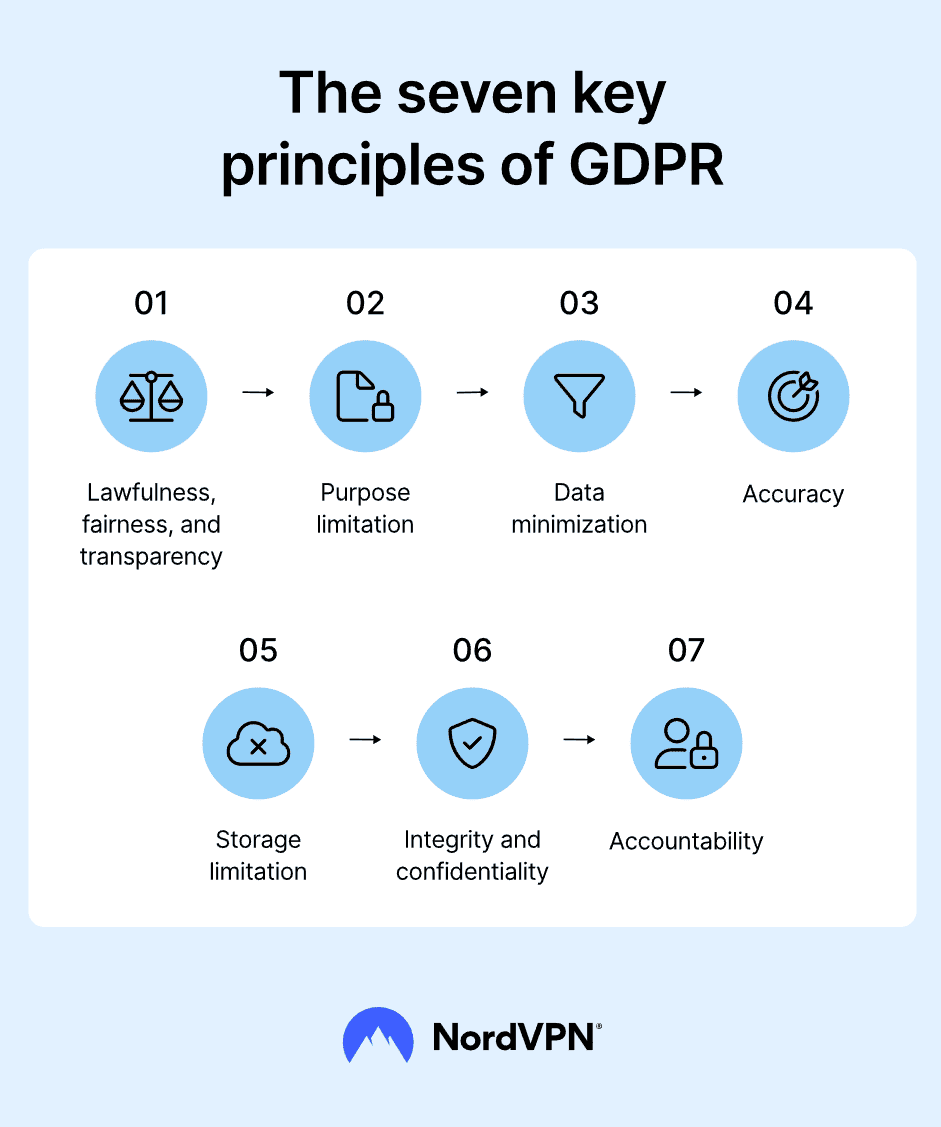
The Legal Landscape: Data Minimization Comes Front and Center
Data minimization—the principle of only keeping data as long as it serves a legitimate business purpose—originated in Europe’s GDPR but is now a mainstay in U.S. state privacy laws. The key message:
Keep personal data only as long as necessary for its original, legitimate purpose.
- GDPR: Requires deletion when data is no longer needed. See NordVPN’s illustration below.
- FTC Safeguards Rule: Financial institutions must dispose of customer info within two years unless there’s a legal/business need.
- CCPA/CPRA (California): Explicit data minimization requirements—don’t keep personal info longer than necessary.
- Other States: 20 U.S. states now have comprehensive data privacy laws; most require data minimization.
- Illinois Biometric Information Privacy Act (BIPA): Strict rules on biometric data retention and destruction.
Takeaway: The regulatory framework is shifting from “keep everything” to “prove why you’re keeping anything.”
The Tension: Retention vs. Minimization
Organizations face a complex balancing act:
- Retention requirements (from laws, contracts, or business needs)
- Minimization requirements (from privacy laws)
- Legal holds for litigation or investigations
Complicating matters, requirements often differ by jurisdiction. The old approach of “keep everything for the longest required period” may not satisfy minimization mandates.
Building a Defensible Program: Best Practices
- Document Everything
- Maintain clear, current records retention schedules with legal and business justifications.
- Document legitimate business purposes for keeping data beyond minimum requirements.
- Break Down Silos
- Form cross-functional governance groups (records management, privacy, IT, legal, and compliance).
- Open communication ensures all perspectives are considered—especially when addressing overlapping requirements (e.g., legal holds).
- Leverage Technology
- Use tools to identify ROT and automate defensible disposition.
- Employ quarantine periods: delete data but hold it in a “soft delete” state before final destruction.
- Automate classification and deletion where possible, with the ability to suspend for legal holds.
- Start Small, Show Wins
- Don’t try to tackle everything at once. Focus on:
- Orphaned/unclaimed file shares
- Legacy systems
- Data obviously beyond all retention periods
- Use data analytics to quantify ROT (“We found 74% rot in the Ann Arbor HR department”) to build your business case.
- Make Disposition a “Must Do”
- Regulators are penalizing over-retention, especially following breaches (see FTC and NY/CA AG enforcement).
- Assume breach: anything you keep is at risk of exposure.
- Don’t Forget Third Parties
- Ensure vendors, law firms, and partners aren’t retaining your data longer than you are.
Overcoming Cultural Resistance
Fear of deleting data is common, rooted in “what if we need it later?” stories. But the risks of keeping unnecessary data far outweigh the rare benefits. Modern AI projects also demand curated, quality data—ROT just gets in the way.
Key Takeaways
- Just start. Don’t let perfection or scale paralyze you—small wins build momentum.
- Use inflection points. System migrations, failed audits, or digital transformation are perfect opportunities to clean house.
- Build defensibility. Consistent, repeatable, and documented processes are your shield in audits and litigation.
- Leverage automation and analytics. Manual review of terabytes is impossible; modern tools make it manageable.
- Stay current. Laws and best practices evolve—so should your program.
Final Thoughts
Risk mitigation in information governance is no longer optional—it’s a business necessity. The landscape is changing quickly, but with the right approach, tools, and cross-functional collaboration, you can reduce risk, control costs, and support compliance.
If you’d like to see how Gimmal’s solutions can help you identify and remediate ROT, automate defensible disposition, or build a stronger governance program, contact us for a demo or proof of concept.
Get Started or Learn More
Watch the full webinar recordings linked in this post.
Request a demo.
See us at upcoming events: AIM, ARMA, and more—check out our events page for more details.
Ready To Speak With Us?
Get started by filling out the form below, and let us help you leverage your existing infrastructure with minimal disruption. Whether you’re looking for ease of use, a single platform solution, or guidance on information governance, we’re here to assist.
Related Content

Podcasts
Podcasts Expert Interviews and Best Practices for Modern Information Governance 23 SEPT Navigating AI and Information Governance Part II – Insights from Gimmal & Office Labs Jason Coggins (Gimmal, UK & Europe) and Mike Nicholas (Office Labs) sit down for a...
Gimmal and Morae: A Game-Changing Partnership in Information Governance
Gimmal and Morae: A Game-Changing Partnership in Information Governance Aug 20, 2025 The information governance (InfoGov) landscape is evolving at a rapid pace, and the recent acquisition of Gimmal by Morae marks a pivotal moment for our industry. In a recent episode...
Navigating AI and Information Governance – Insights from Gimmal & OfficeLabs
Navigating AI and Information Governance – Insights from Gimmal & OfficeLabs Jul 8, 2025 In a recent episode of the Gimmal Podcast, Jason Coggins (Gimmal, UK & Europe) and Graham Bidwell (OfficeLabs) sat down for a deep dive into the fast-evolving worlds of...
End-to-End Email Records Management: How Gimmal & Colligo Are Automating Compliance for Modern Organizations
End-to-End Email Records Management: How Gimmal & Colligo Are Automating Compliance for Modern Organizations May 7, 2025 Managing records in a modern organization is no easy feat—especially when so much critical business information flows through email. That’s why...
Gimmal Extends Microsoft Purview Information Protection Solution for Enhanced Sensitive Data Labeling and Governance
Thursday, June 20, 2024 – HOUSTON, TX – Gimmal, the market’s only end-to-end information governance platform, announced today the launch of their Microsoft Purview Sensitivity Labels solution to extend and enhance sensitive data classification for unstructured...
